In today’s API-driven world, authentication and authorization are foundational to secure application design. Modern systems—especially microservices, mobile apps, and single-page applications (SPAs)—often rely on JWT vs OAuth 2.0 to handle identity.
However, these two terms often appear together, leading to confusion. Are they competitors? Do they do the same thing?
The short answer is: No. They serve different purposes and solve different problems. This article will break down what each technology does, how they work, and when to use them effectively.
1. What Is JWT (JSON Web Token)?
A JWT (JSON Web Token) is a compact, stateless token format used to transmit claims between parties securely.
It is an encoded (not encrypted) string containing three parts, separated by dots (.):
-
Header
-
Payload
-
Signature
Example Structure: header.payload.signature
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
eyJ1c2VyX2lkIjoxMjMsInJvbGUiOiJhZG1pbiJ9.
dBjftJeZ4CVP-mB92K27uhbUJU1p1r_wW1gFWFOEjXk
Key Characteristics of JWT:
-
Stateless: No need for server-side session storage (like Redis or SQL).
-
Digitally Signed: Verified using HMAC (symmetric) or RSA/ECDSA (asymmetric).
-
Custom Claims: Can contain User ID, roles, and permissions.
-
Performance: Fast to verify since no database lookup is needed.
⚠️ Common Misunderstanding:
JWTs are not encrypted by default. They are only base64-encoded. Never put sensitive information (like passwords or social security numbers) in a JWT payload unless you use JWE (JSON Web Encryption).
2. What Is OAuth 2.0?
OAuth 2.0 is an industry-standard authorization framework. It allows applications to access resources on behalf of a user without sharing credentials.
Real-world Example:
When you see “Login with Google,” that is OAuth 2.0. Google issues access tokens so your app can read the user’s email or profile without ever seeing their Google password.
Core OAuth 2.0 Roles:
-
Resource Owner: The user.
-
Client: The application requesting access.
-
Authorization Server: The server issuing tokens (e.g., Google, Okta, Auth0).
-
Resource Server: The API providing protected data.
What OAuth DOES:
-
Delegates access.
-
Defines token generation flows (Grant Types).
-
Manages user consent.
What OAuth DOESN’T Do:
-
It does not define the token structure (it can use random strings or JWTs).
-
It does not handle user authentication natively (that is handled by OpenID Connect).
3. JWT vs OAuth 2.0: The Key Differences
To clear up the confusion, here is a direct comparison:
| Feature | JWT | OAuth 2.0 |
| Purpose | Token format (Container) | Authorization framework (Protocol) |
| Handles Login? | ❌ No | ❌ No (OIDC does) |
| Stateless? | Yes | Depends on implementation |
| Token Type | Self-contained | Any (Random string or JWT) |
| Primary Use | Information exchange | Delegated authorization |
Important Note:
-
JWT is NOT an authentication framework.
-
OAuth 2.0 is NOT an identity framework.
-
To authenticate users using OAuth, you need OpenID Connect (OIDC) on top.
4. How They Work Together
OAuth 2.0 can issue many token formats. JWT is simply one of them.
In modern systems, OAuth 2.0 access tokens are usually implemented as JWTs because:
-
Self-contained: The Resource Server (API) can validate the token without calling the Authorization Server.
-
Performance: Reduces network latency and database lookups.
-
Scalability: Ideal for distributed microservices.
The Typical Flow:
-
User logs in via an OAuth 2.0 Authorization Server.
-
Server issues a JWT Access Token (+ optional Refresh Token).
-
Client sends the JWT to the API on every request.
-
API verifies the JWT signature and claims locally.
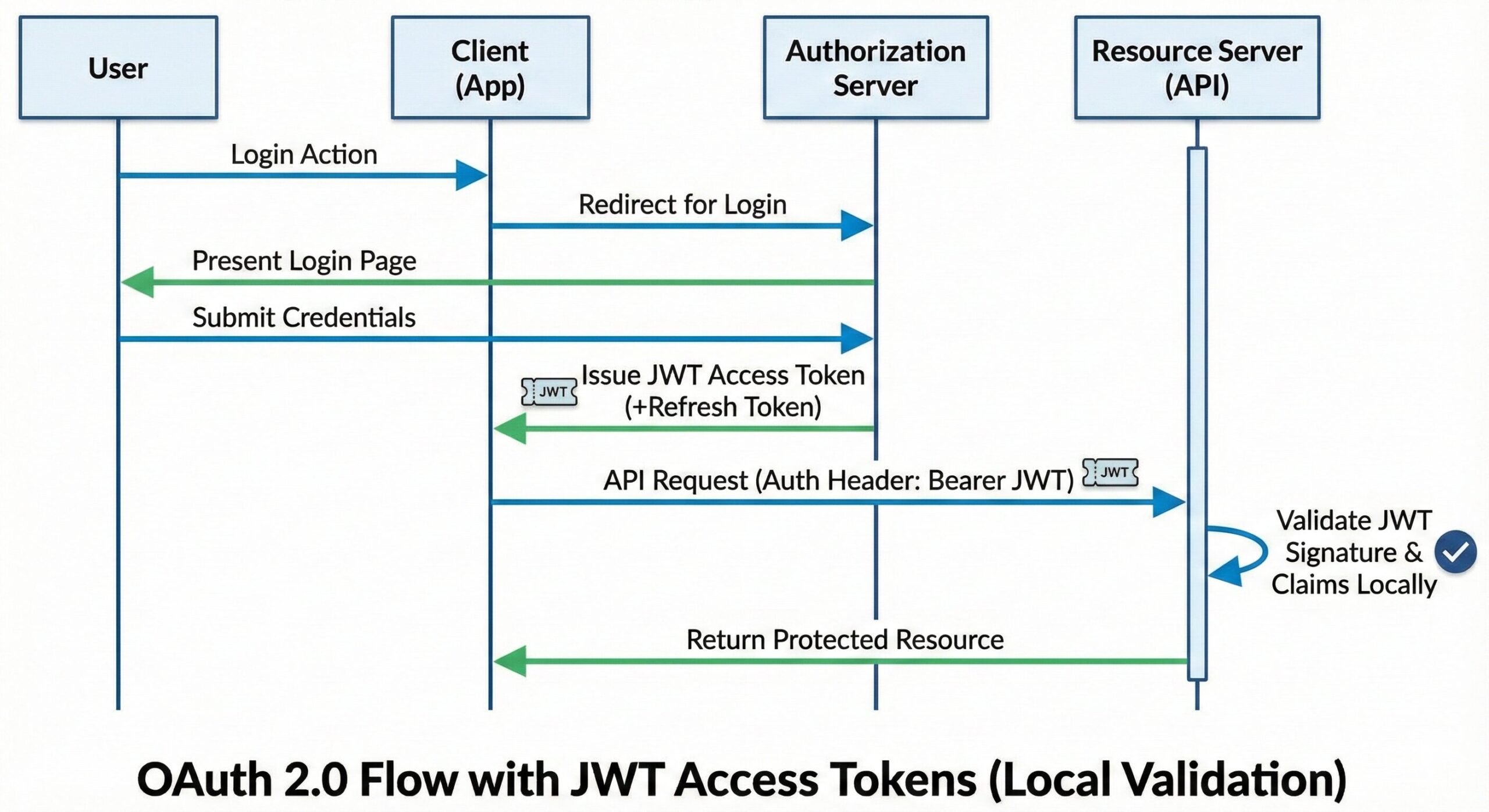
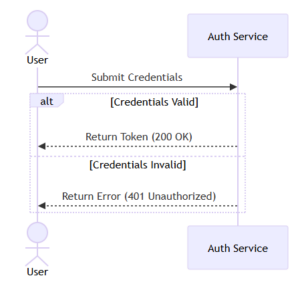
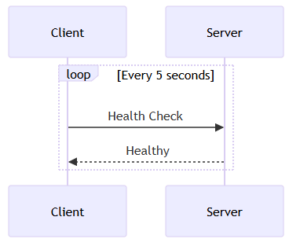
-
Description: A sequence diagram showing the flow: Client -> Auth Server (returns JWT) -> Client -> API (validates JWT).
-
Alt Text: OAuth 2.0 flow using JWT Access Tokens.
5. Access Token vs. Refresh Token
-
Access Token: Short-lived (e.g., 15 minutes). Sent with every API request. Usually a JWT.
-
Refresh Token: Long-lived (days/weeks). Used to obtain new access tokens when the old one expires. Never share this with the Resource Server.
6. Security Best Practices
Both technologies are powerful but dangerous if misused. Follow these rules to secure your app.
JWT Best Practices:
-
Short Expiration: Keep
exptime short (5-15 mins). -
Secure Storage: Store tokens in HttpOnly, Secure Cookies (not
localStorage) to prevent XSS attacks. -
Algorithm: Use asymmetric signing (RS256) for distributed systems.
OAuth 2.0 Best Practices:
-
PKCE: Always use Authorization Code Flow with PKCE for mobile and SPAs.
-
No Implicit Flow: Never use the deprecated Implicit Flow.
-
Least Privilege: Request only the scopes you absolutely need.
-
Token Rotation: Rotate refresh tokens upon every use to detect theft.
Conclusion
JWT and OAuth 2.0 are core technologies in modern architecture. Although they are often used together, they solve distinct problems:
-
JWT is a format for securely transmitting information.
-
OAuth 2.0 is a protocol for delegating access.
Understanding their roles will help you build secure, scalable identity systems for web, mobile, and distributed applications.
References
Ready to get started?
Contact IVC for a free consultation and discover how we can help your business grow online.
Contact IVC for a Free Consultation